Elasticsearch Indexing Strategy in Asset Management Platform (AMP)
The Netflix TechBlog
MARCH 10, 2023
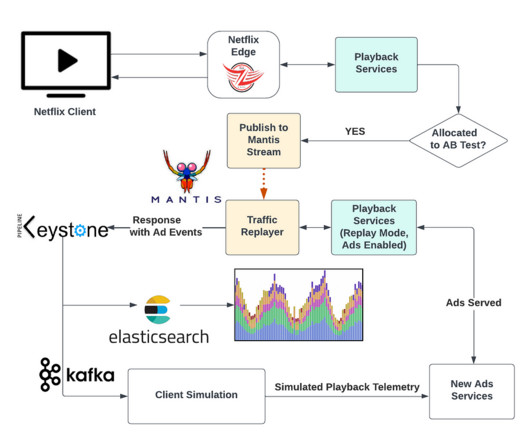
It provides simple APIs for creating indices, indexing or searching documents, which makes it easy to integrate. Mapping is used to define how documents and their fields are supposed to be stored and indexed. All the assets of a specific type use the specific index defined for that asset type to create or update the asset document.











































Let's personalize your content