Log4j 2 Vulnerability: Identifying and Minimizing Production Risk
Dynatrace
DECEMBER 12, 2021
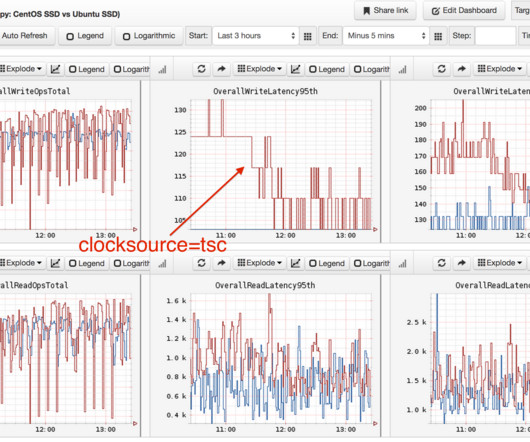
The National Vulnerability Database describes the exploit here. As organizations work to find the usage of this library in their applications, they should focus on three criteria to prioritize the fix in their environment: Public Internet Exposure – Are the Java processes using these libraries directly accessible from the internet?








































Let's personalize your content