CSS and Network Performance
CSS Wizardry
NOVEMBER 9, 2018
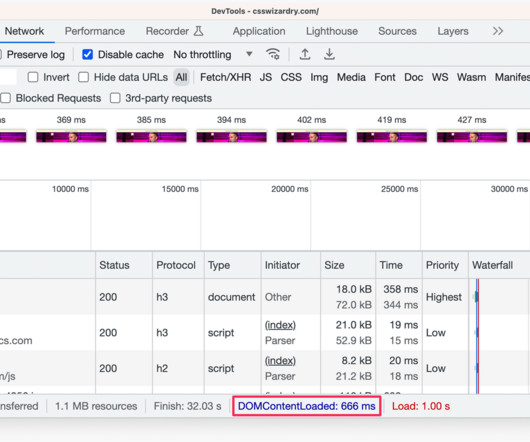
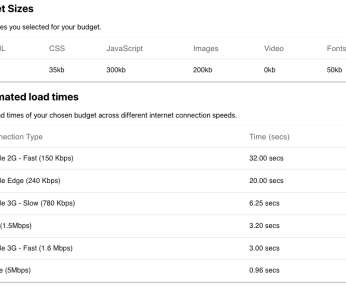
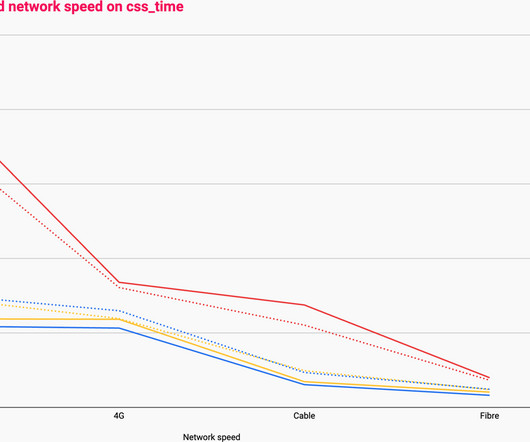
In this post I want to look at how CSS can prove to be a substantial bottleneck on the network (both in itself and for other resources) and how we can mitigate it, thus shortening the Critical Path and reducing our time to Start Render. This article is getting way, way more forensic than I intended. Employ Critical CSS.





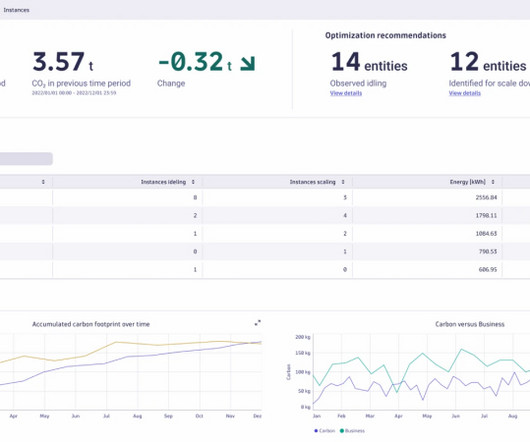

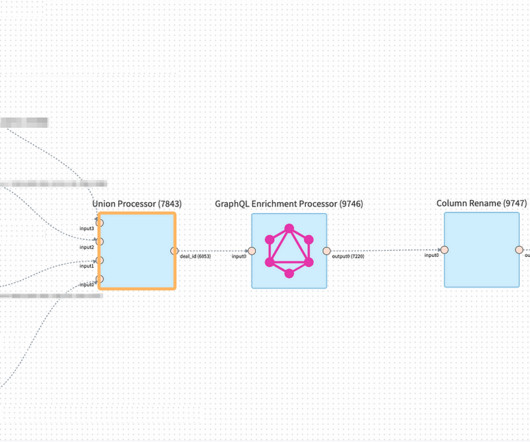































Let's personalize your content