Three smart log ingestion strategies in Dynatrace (without OneAgent)
Dynatrace
DECEMBER 15, 2022
In this blog, we share three log ingestion strategies from the field that demonstrate how building up efficient log collection can be environment-agnostic by using our generic log ingestion application programming interface (API). Log ingestion strategy no. Log ingestion strategy No. Log ingestion strategy No.







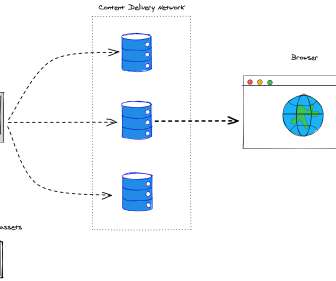





























Let's personalize your content