What is RASP? Why runtime application self-protection is important, and how to do it right
Dynatrace
JUNE 16, 2022
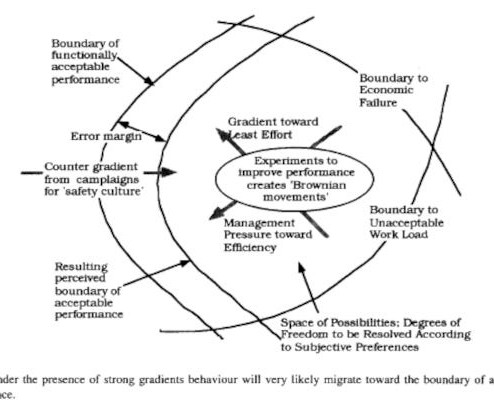
In 2012, Gartner coined the term RASP to characterize this approach, which brings the security perimeter right to the application itself. With RASP technology, you can distinguish between genuine information requests and malicious attacks. It can control application execution as well as detect and block real-time attacks.







































Let's personalize your content