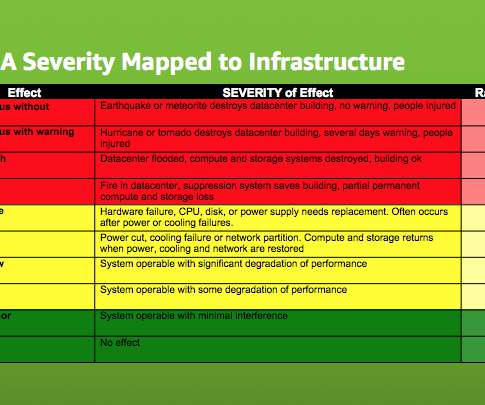
Vulnerability assessment: key to protecting applications and infrastructure
Dynatrace
OCTOBER 13, 2021
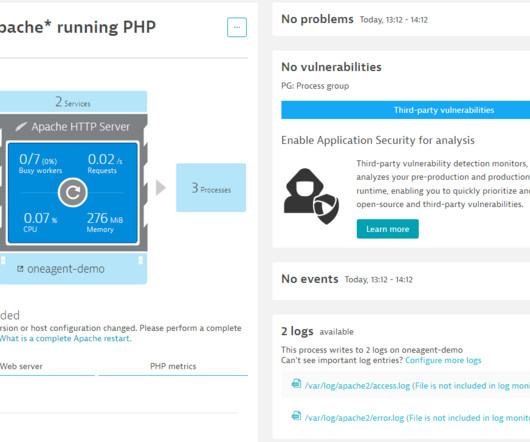
Protecting IT infrastructure, applications, and data requires that you understand security weaknesses attackers can exploit. Vulnerability assessment is the process of identifying, quantifying, and prioritizing the cybersecurity vulnerabilities in a given IT system. NMAP is an example of a well-known open-source network scanner.






































Let's personalize your content