For your eyes only: improving Netflix video quality with neural networks
The Netflix TechBlog
NOVEMBER 17, 2022
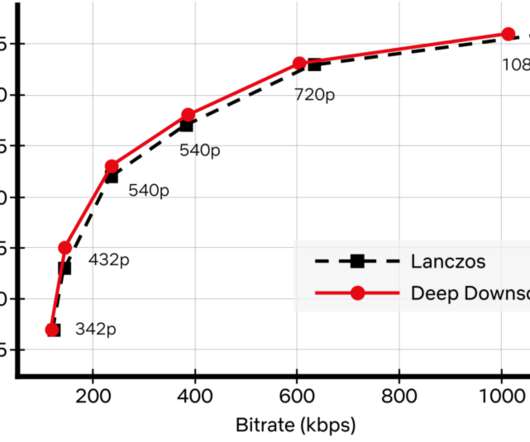
For example, we invest in next-generation, royalty-free codecs and sophisticated video encoding optimizations. Recently, we added another powerful tool to our arsenal: neural networks for video downscaling. How can neural networks fit into Netflix video encoding? Video encoding using a conventional video codec, like AV1.












































Let's personalize your content