Security operations centers: How state governments can enhance cybersecurity posture
Dynatrace
APRIL 3, 2024
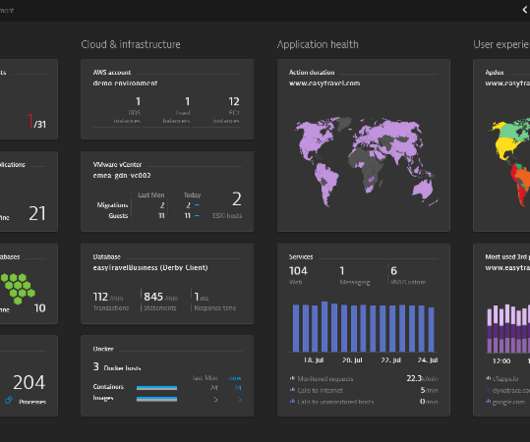
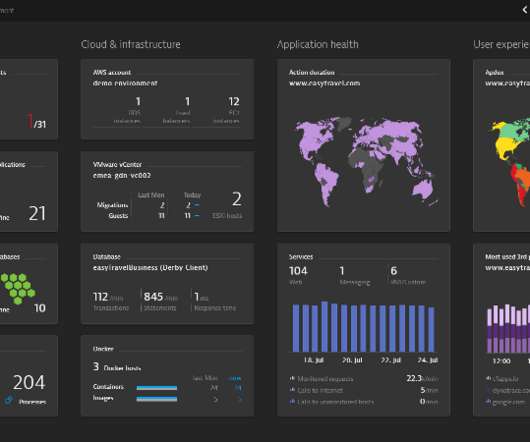
As a result, they may fail to consider the importance of full-stack observability, dashboards, AI-driven automation, application security, and other factors when designing their security operations strategy. What is a security operations center? Dynatrace immediately identified Log4Shell and the first attempted attack patterns.









































Let's personalize your content