Practical business process monitoring for real-time business observability
Dynatrace
FEBRUARY 9, 2024
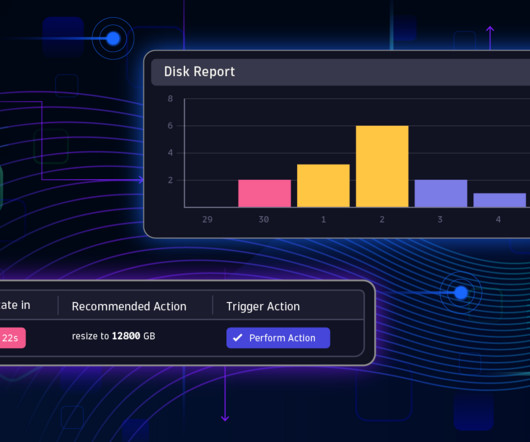
One of the more popular use cases is monitoring business processes, the structured steps that produce a product or service designed to fulfill organizational objectives. OneAgent business events require no code changes, just a simple configuration to define capture rules. Getting started is simple.







































Let's personalize your content