Why vulnerability management enhances your cloud application security strategy
Dynatrace
JANUARY 21, 2022
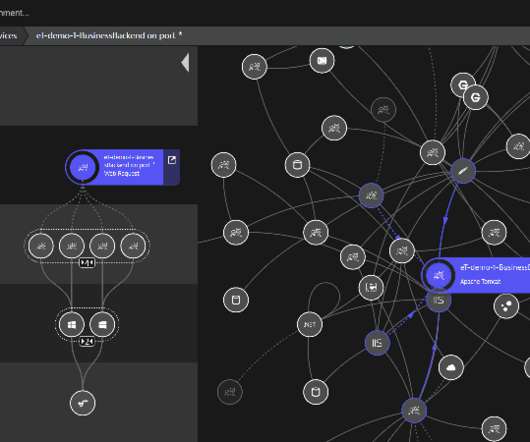
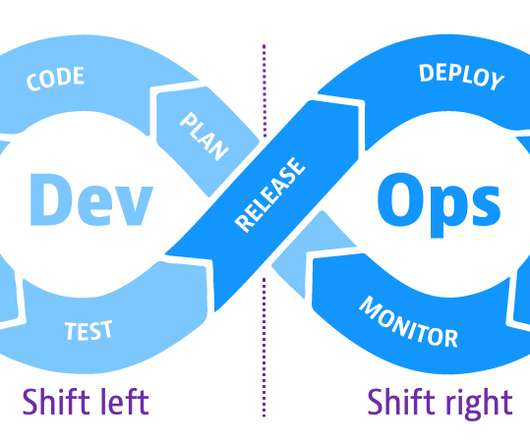
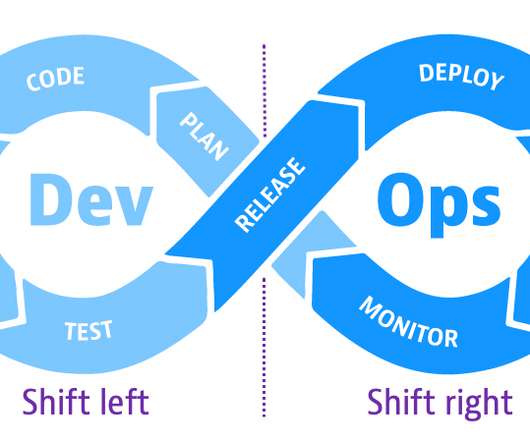
Without a centralized approach to vulnerability management, DevSecOps teams waste time figuring out how a vulnerability affects the production environment and which systems to fix first. The post Why vulnerability management enhances your cloud application security strategy appeared first on Dynatrace blog. Contextual insight.








































Let's personalize your content