What is software automation? Optimize the software lifecycle with intelligent automation
Dynatrace
JUNE 26, 2023
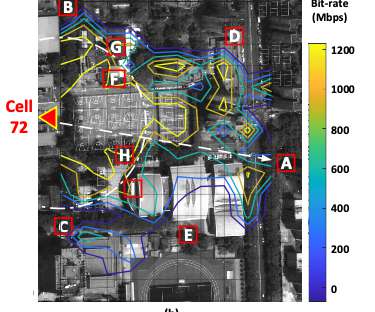
The core benefits of an AIOps-automated software analytics platform include the following: Infrastructure monitoring. Investigate network systems and application security incidents quickly for near-real-time remediation. These include mobile, web, Internet of Things, and application programming interfaces. Application security.







































Let's personalize your content