How to achieve the pillars of zero trust at federal agencies
Dynatrace
FEBRUARY 12, 2024
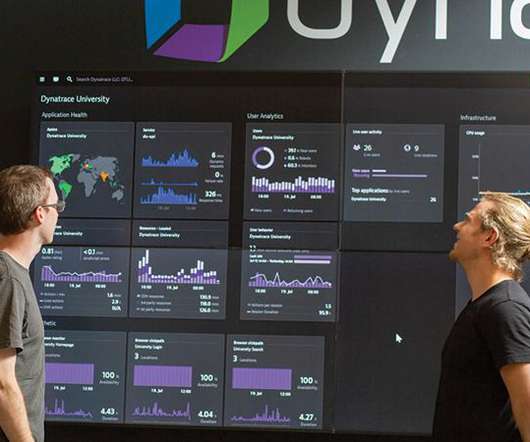
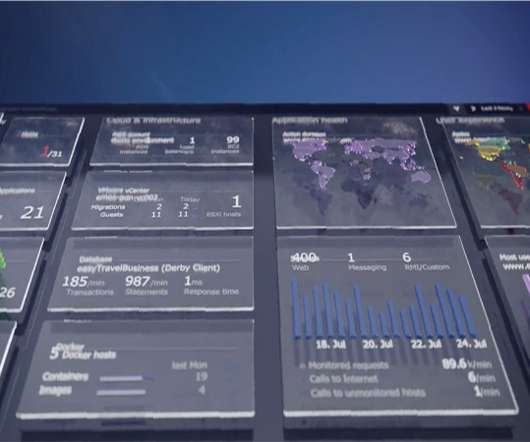
Government Toward Zero Trust Cybersecurity Principles , have increased federal IT and security leaders’ urgency to implement zero trust (ZT). Zero trust (ZT) mandates never trusting—but always verifying—any actor, system, network, or service operating outside or within the security perimeter, according to the OMB memo.



































Let's personalize your content