Reinventing virtualization with the AWS Nitro System
All Things Distributed
SEPTEMBER 14, 2020
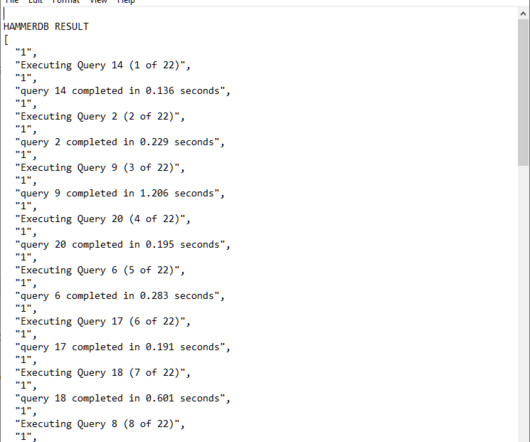
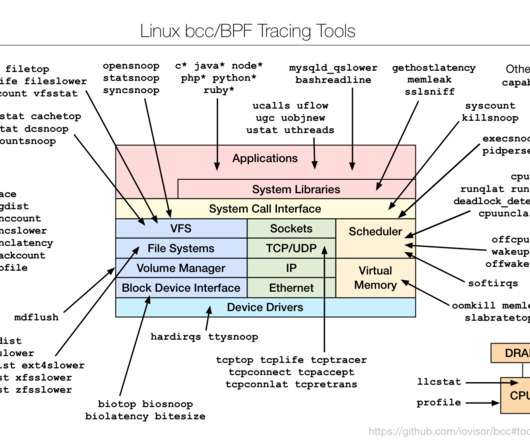
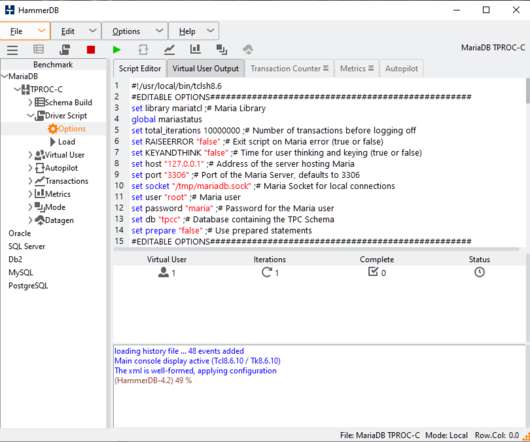
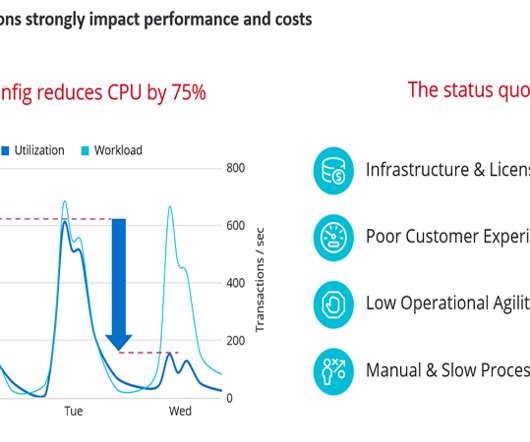
A great example of this approach to innovation and problem solving is the creation of the AWS Nitro System , the underlying platform for our EC2 instances. Now, with the Nitro System, we can offer the best price performance in the cloud, the most secure environment, and a faster pace of innovation.









































Let's personalize your content