Using Raspberry PI in Virtualization: Unlocking New Possibilities
DZone
JANUARY 3, 2024
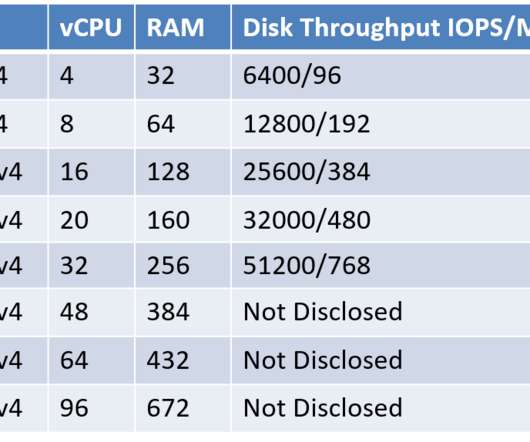
Through the use of virtualization technology, multiple operating systems can now run on a single physical machine, revolutionizing the way we use computer hardware.










































Let's personalize your content