RSA 2022 guide: DevSecOps transformation with runtime vulnerability management
Dynatrace
MAY 23, 2022
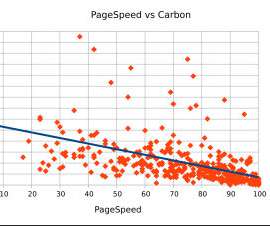
Cloud environment toolkits —microservices, Kubernetes, and serverless platforms — deliver business agility, but also create complexity for which many security solutions weren’t designed. See how causation-based AIOps is a game-changer. Especially, how your organization can speed risk analysis, remediation, and collaboration with Davis.




























Let's personalize your content