C++20 approved, C++23 meetings and schedule update
Sutter's Mill
SEPTEMBER 6, 2020
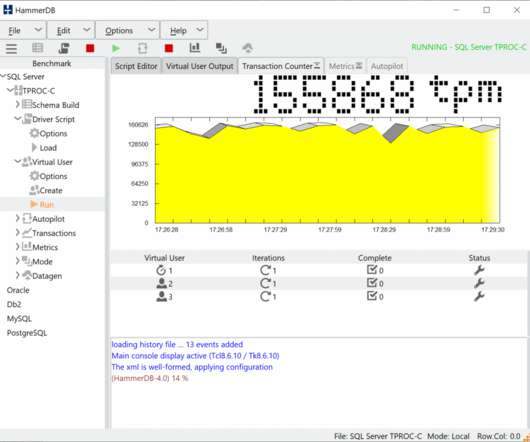
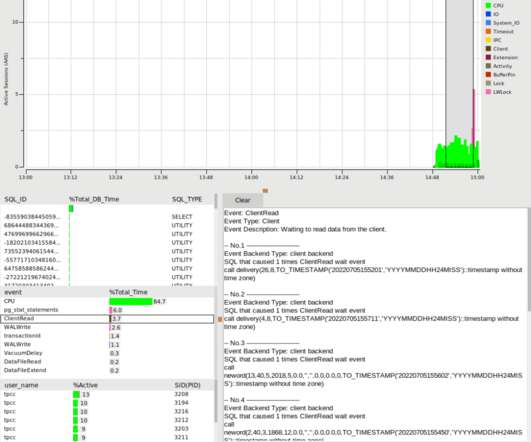
A couple of interesting things happened in the ISO C++ world this week… C++20 passed unanimously, on track to publish later this year On Friday September 4, C++20’s DIS (Draft International Standard) ballot ended, and it passed unanimously.






































Let's personalize your content