Why business digital transformation is still a key C-level priority today
Dynatrace
MARCH 28, 2024
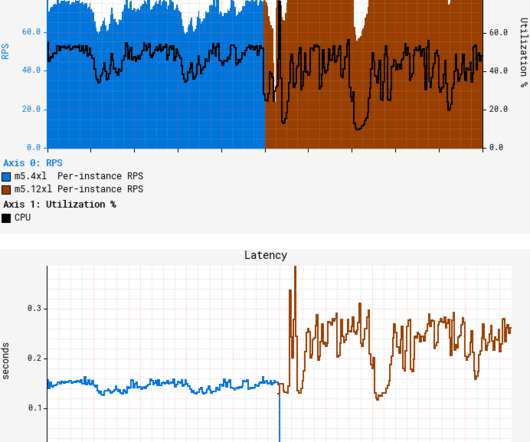
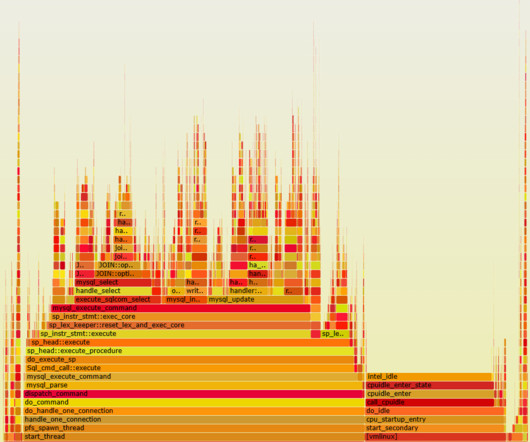
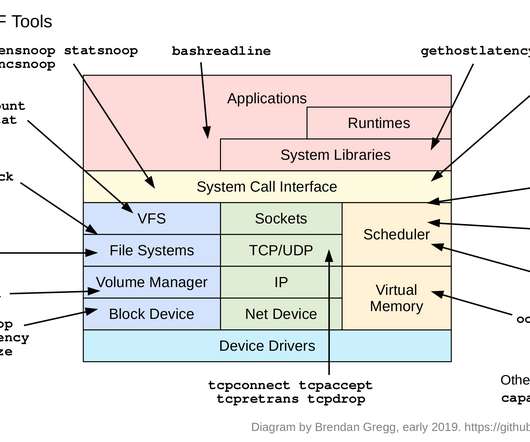
According to a recent Thomson Reuters survey, nearly 50% of C-level executives said that business digital transformation was their top priority over the next 18 months, followed by reducing costs (44%) and increasing customer satisfaction (44%). And according to Statista , $2.4 trillion will be spent on digital transformation on 2024.







































Let's personalize your content