Pivoting to a total experience strategy: A necessity for governments today
Dynatrace
MARCH 14, 2024
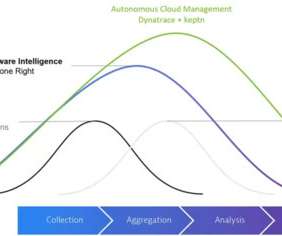
Today, citizens are no longer passive recipients of government services, but rather active participants in a digital age. From mobile applications to websites, government services must be accessible, available, and performant for those who rely on them. Everything impacts and influences each other.

















Let's personalize your content