Don’t Start Using Your MySQL Server Until You’ve Configured Your OS
Percona
SEPTEMBER 28, 2023
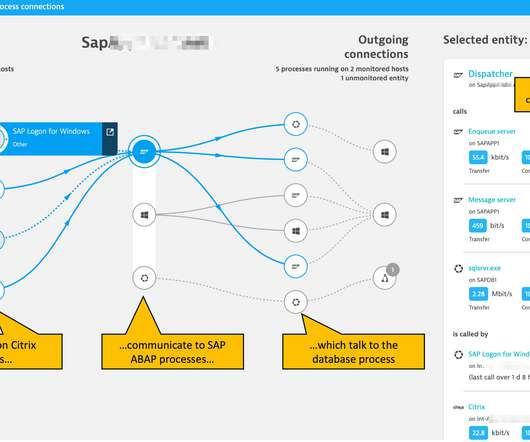
Whenever you install your favorite MySQL server on a freshly created Ubuntu instance, you start by updating the configuration for MySQL, such as configuring buffer pool, changing the default datadir director, and disabling one of the most outstanding features – query cache. It’s a nice thing to do, but first things first.












































Let's personalize your content