Why digital transformation hinges on SRE teams
Dynatrace
SEPTEMBER 21, 2022
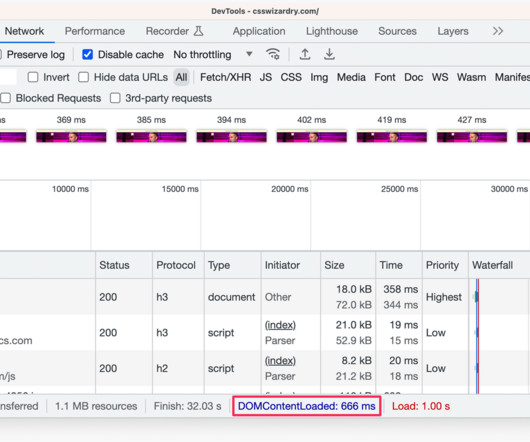
Additionally, 60% report spending much of their time building and maintaining automation code. While creating automation scripts might be an effective short-term solution, it requires long-term maintenance and code updates, which become more complicated as environments become more complex.





































Let's personalize your content