APRA CPS 230 compliance, explained
Dynatrace
NOVEMBER 2, 2023
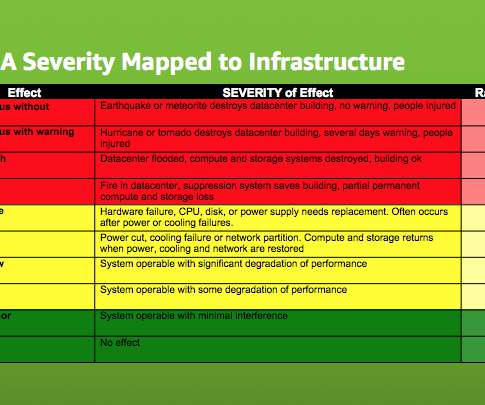
If your organisation is involved in achieving APRA compliance, you are likely facing the daunting effort of de-risking critical system delivery. Moreover, for banking organisations, there is a good chance some of those systems are outdated. Observability aims to interpret them all in real time.










































Let's personalize your content