Rapid Event Notification System at Netflix
The Netflix TechBlog
FEBRUARY 18, 2022
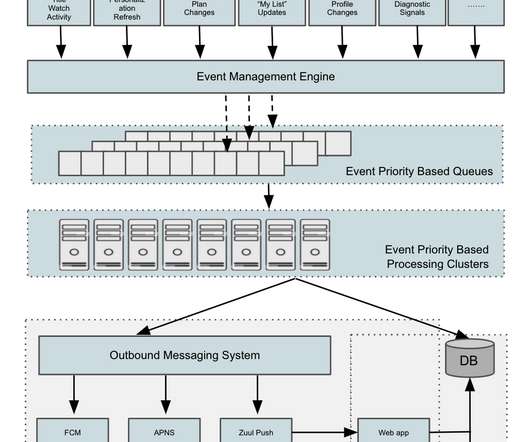
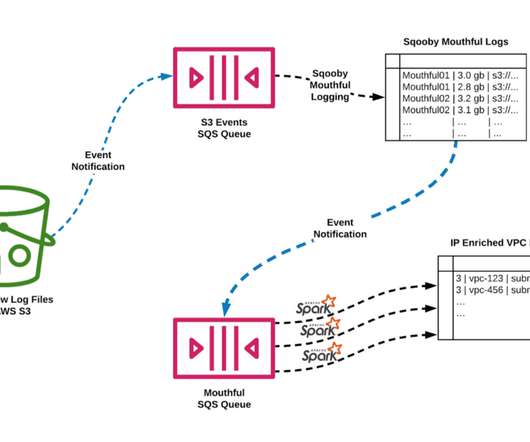
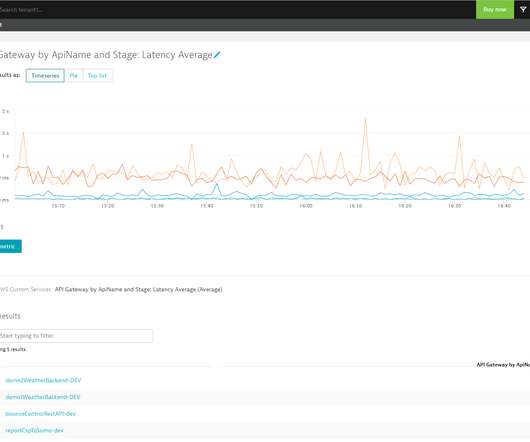
To this end, we developed a Rapid Event Notification System (RENO) to support use cases that require server initiated communication with devices in a scalable and extensible manner. In this blog post, we will give an overview of the Rapid Event Notification System at Netflix and share some of the learnings we gained along the way.






































Let's personalize your content