Leveraging ML-Based Anomaly Detection for 4G Networks Optimization
DZone
JANUARY 14, 2023
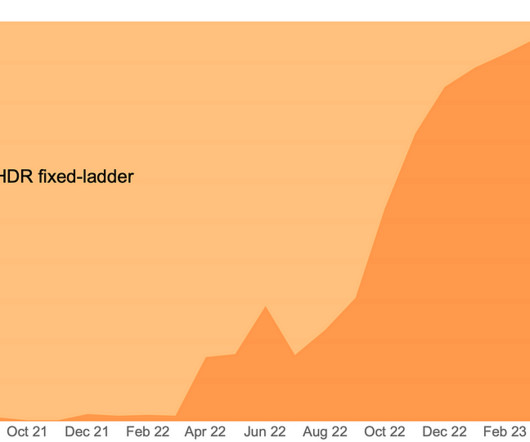
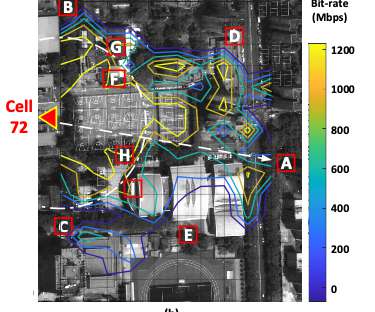
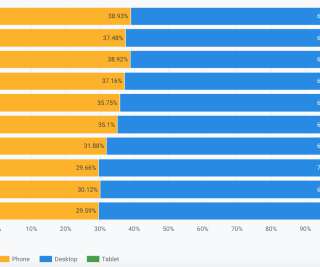
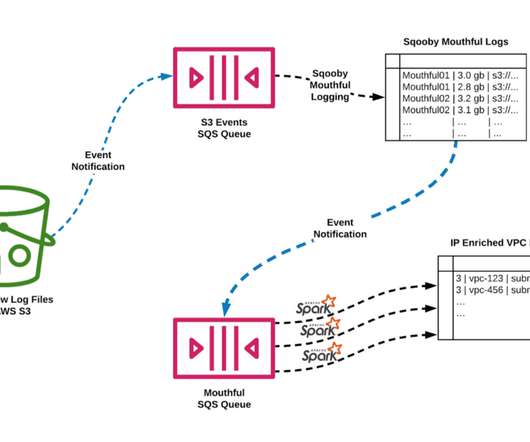
While the technology is far from perfect, the advancements in ML allow other industries to benefit as well. In this article, we will look at our own research on how to make the operations of internet providers more effective. As an example, you can envision a massive area with big cities, little towns, or forests that span for miles.











































Let's personalize your content