Pre-Deployment Policy Compliance
Abhishek Tiwari
JULY 22, 2023
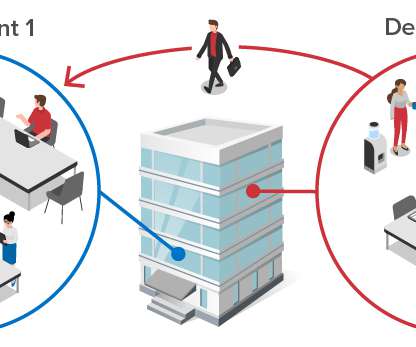
In the fast-paced world of software development, the ability to deploy applications quickly and efficiently is crucial for organizations. However, amidst the drive for speed, ensuring policy compliance is often overlooked, leading to potential security vulnerabilities and compliance risks.























Let's personalize your content