Bring syslog into Dynatrace using OpenTelemetry to get open source value with enterprise support
Dynatrace
MARCH 15, 2024
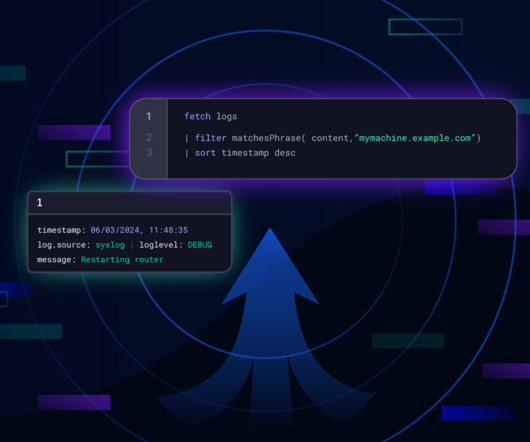
Getting insights into the health and disruptions of your networking or infrastructure is fundamental to enterprise observability. Syslog is a protocol with clear specifications that require a dedicated syslog server. Refer to F5 BIG-IP documentation for detailed and up-to-date instructions regarding remote Syslog configuration.











































Let's personalize your content