mysqldump Best Practices: Part 2 – Migrations Guide
Scalegrid
APRIL 9, 2021
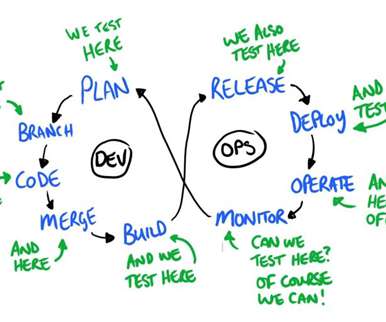
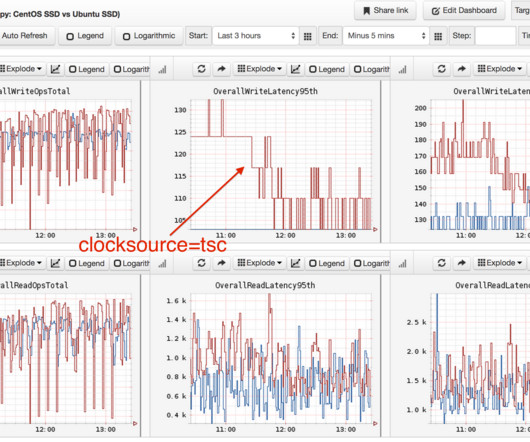
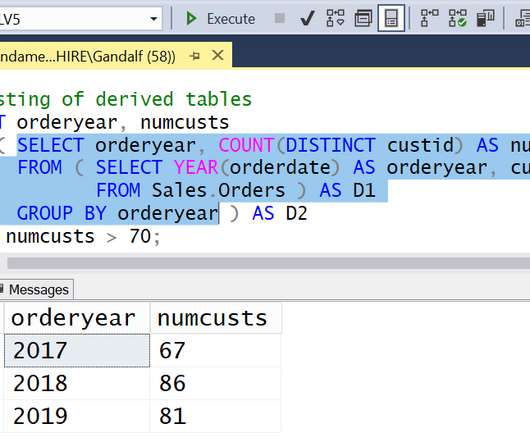
In the second and final part of our mysqldump best practices we will talk about how to handle the migration and import for stored program objects and views from your MySQL database.







































Let's personalize your content