How to overcome the cloud observability wall
Dynatrace
DECEMBER 8, 2021
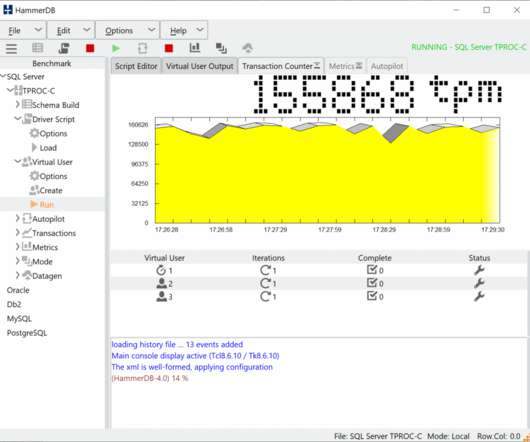
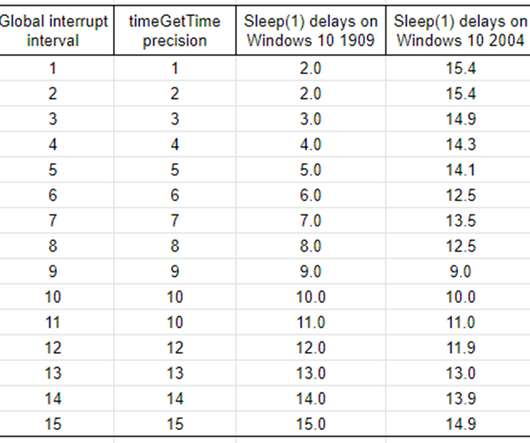
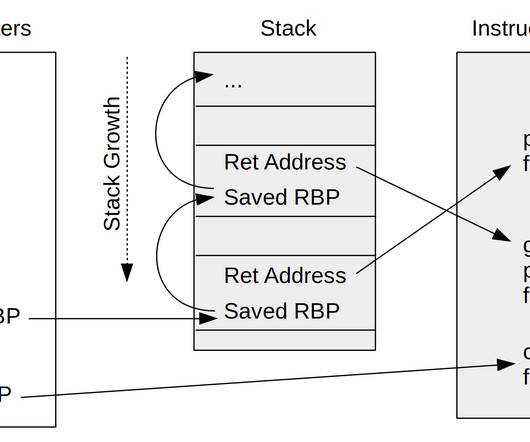
There are a few important details worth unpacking around monolithic observability as it relates to these qualities: The nature of a monolithic application using a single programming language can ensure all code uses the exact same logging standards, location, and internal diagnostics. Just as the code is monolithic, so is the logging.









































Let's personalize your content