What is Log4Shell? The Log4Shell vulnerability explained (and what to do about it)
Dynatrace
DECEMBER 16, 2021
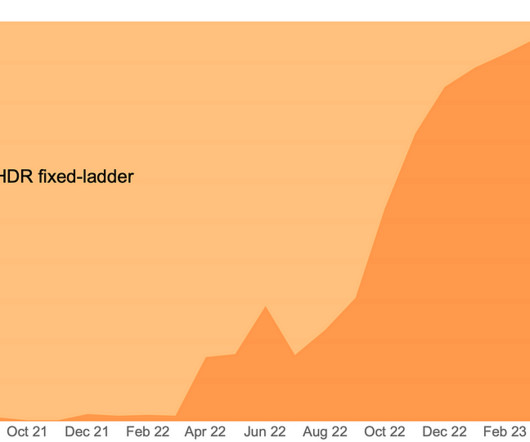
Since December 10, days after a critical vulnerability known as Log4Shell was discovered in servers supporting the game Minecraft, millions of exploit attempts have been made of the Log4j 2 Java library, according to one team tracking the impact, with potential threat to millions more applications and devices across the globe. Dynatrace news.

































Let's personalize your content