New SNMP platform extensions provide observability at scale for network devices
Dynatrace
NOVEMBER 24, 2021
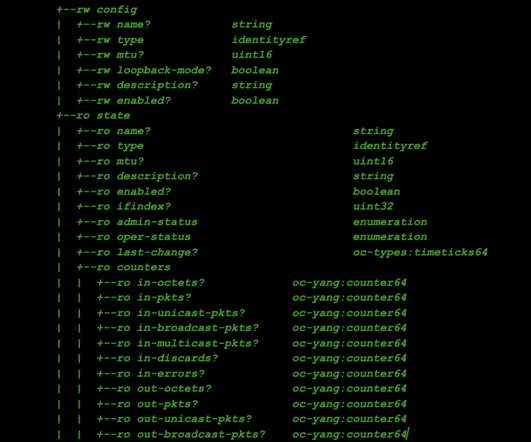
Quick and easy network infrastructure monitoring. Begin network monitoring by simply deploying an extension with just a few clicks. The topology model for network devices covers simple to complex use cases from visualizing the interfaces of a router to mapping an F5 Big-IP LTM load balancer. Virtual servers. Pool nodes.








































Let's personalize your content