How Netflix brings safer and faster streaming experience to the living room on crowded networks…
The Netflix TechBlog
APRIL 20, 2020
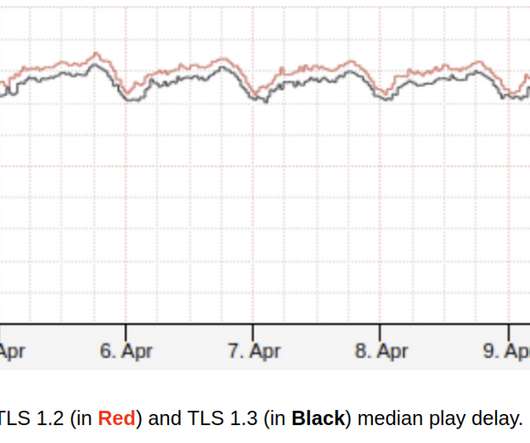
How Netflix brings safer and faster streaming experience to the living room on crowded networks using TLS 1.3 We want playback to start instantly and to never stop unexpectedly in any network environment. for streaming traffic. handshake was not designed to protect the integrity of the entire handshake. What is TLS?










































Let's personalize your content