Unlock end-to-end observability insights with Dynatrace PurePath 4 seamless integration of OpenTracing for Java
Dynatrace
DECEMBER 9, 2020
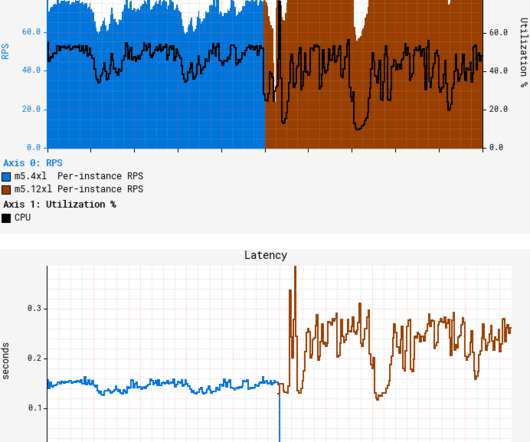
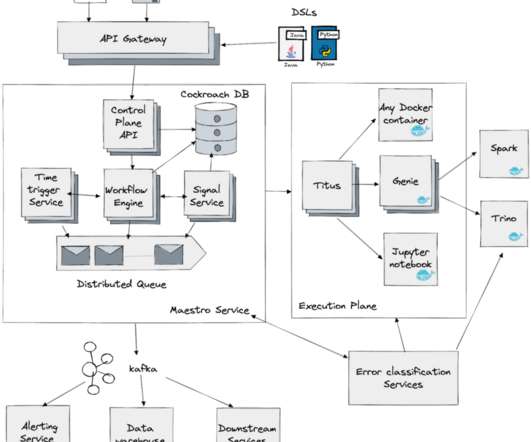
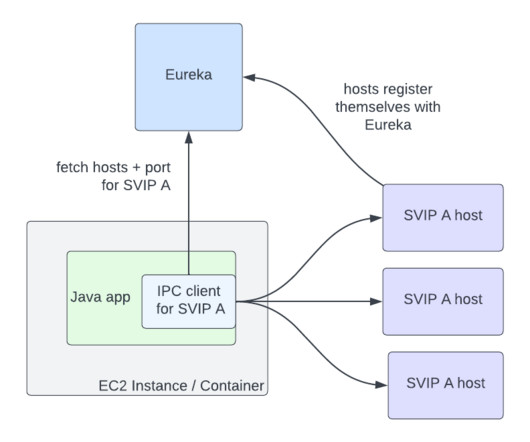
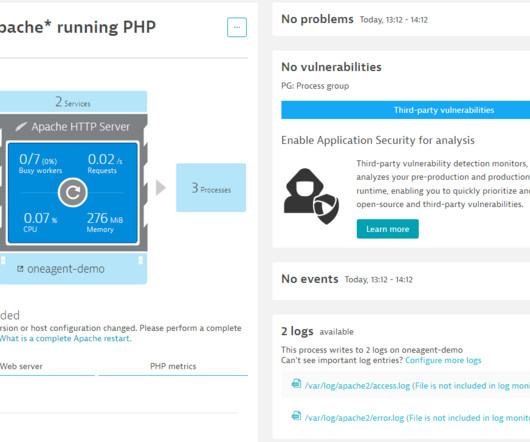
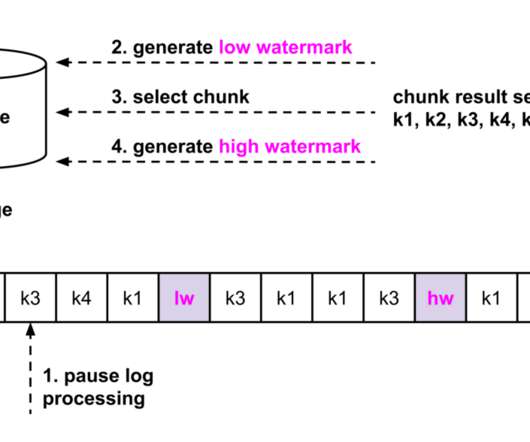
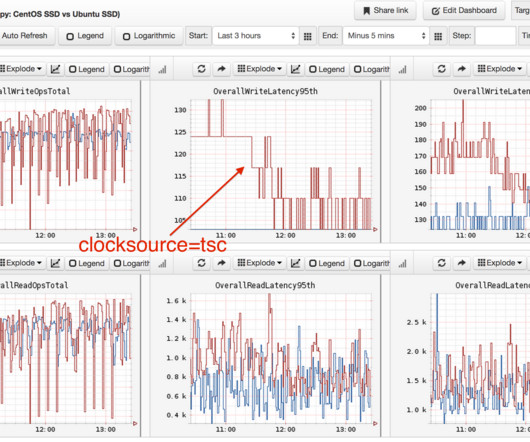
Cloud-native technologies and microservice architectures have shifted technical complexity from the source code of services to the interconnections between services. Deep-code execution details. With Dynatrace OneAgent you also benefit from support for traffic routing and traffic control. Dynatrace news.









































Let's personalize your content