Dynatrace accelerates business transformation with new AI observability solution
Dynatrace
JANUARY 31, 2024
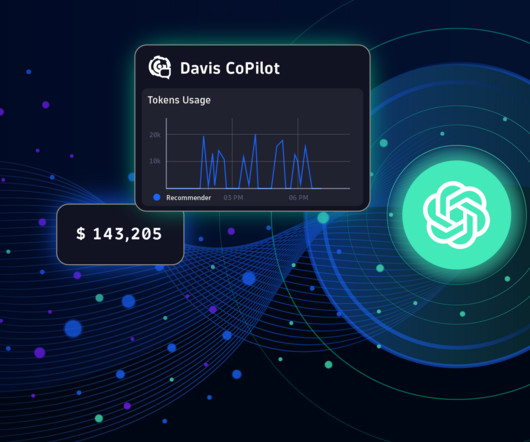
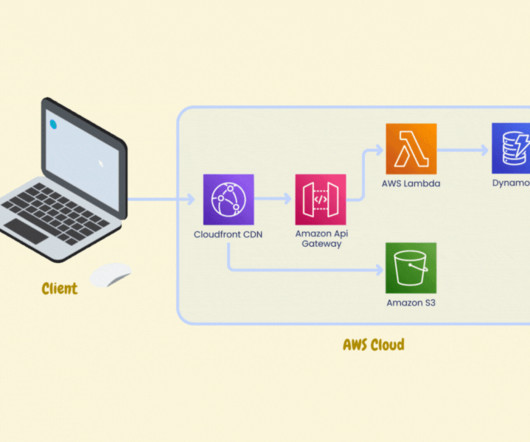
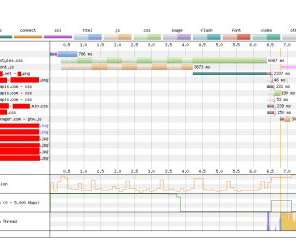
GenAI is prone to erratic behavior due to unforeseen data scenarios or underlying system issues. The RAG process begins by summarizing and converting user prompts into queries that are sent to a search platform that uses semantic similarities to find relevant data in vector databases, semantic caches, or other online data sources.













































Let's personalize your content