Best Practices in Cloud Security Monitoring
Scalegrid
JANUARY 11, 2024
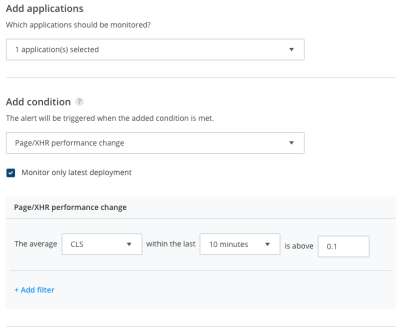
This article strips away the complexities, walking you through best practices, top tools, and strategies you’ll need for a well-defended cloud infrastructure. Get ready for actionable insights that balance technical depth with practical advice.





































Let's personalize your content