Evaluating the Evaluation: A Benchmarking Checklist
Brendan Gregg
JUNE 30, 2018
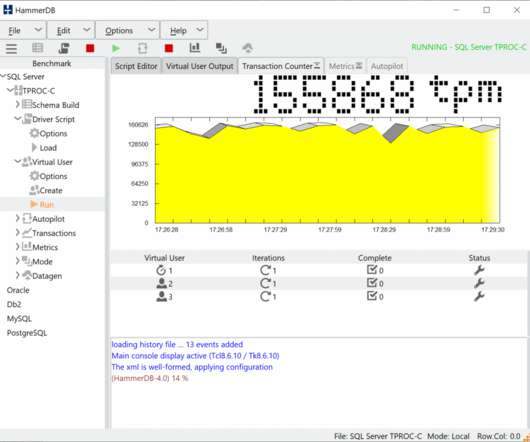
A co-worker introduced me to Craig Hanson and Pat Crain's performance mantras, which neatly summarize much of what we do in performance analysis and tuning. These have inspired me to summarize another performance activity: evaluating benchmark accuracy. If the benchmark reported 20k ops/sec, you should ask: why not 40k ops/sec?



























Let's personalize your content