Dynatrace EdgeConnect securely connects your local systems to Dynatrace SaaS
Dynatrace
OCTOBER 10, 2023
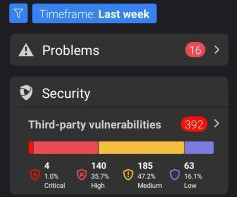
We’ve developed an EdgeConnect Management app to assist you in configuring host and domain name patterns while observing the availability status of your existing EdgeConnect instances. It supports multi-instance high availability and load balancing, providing robust performance and reliability.











































Let's personalize your content