Driving your FinOps strategy with observability best practices
Dynatrace
MARCH 18, 2024
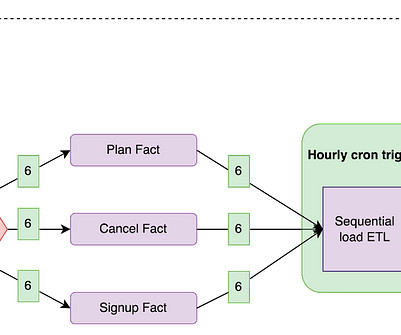
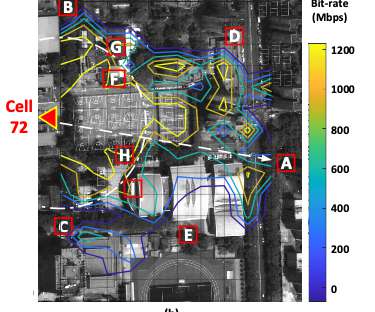
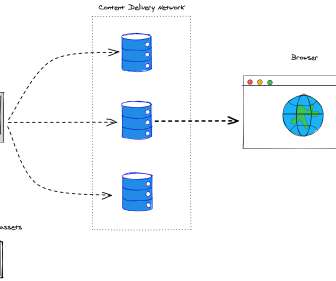
In response, many organizations are adopting a FinOps strategy. Suboptimal architecture design. Observability tools can provide insights into resource utilization metrics, such as CPU usage, memory usage, and network throughput. Dynatrace can help you achieve your FinOps strategy using observability best practices.










































Let's personalize your content