Network performance monitoring top of mind for CloudOps teams
Dynatrace
MAY 19, 2023
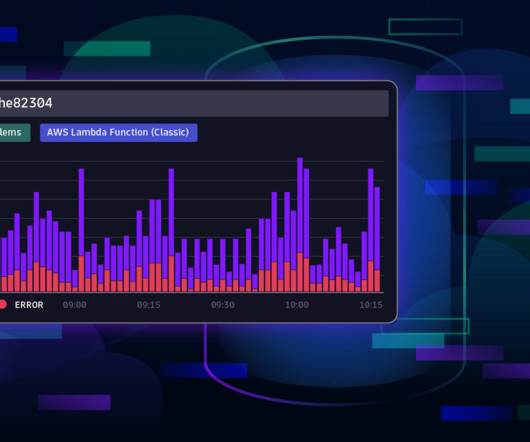
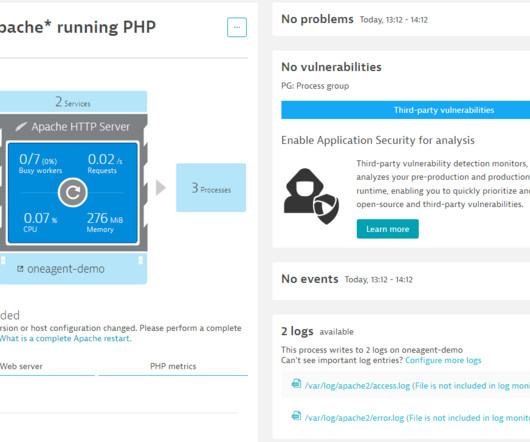
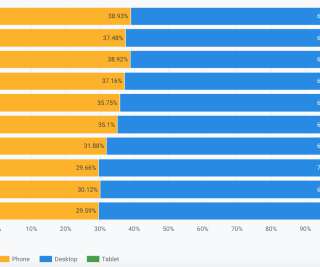
For cloud operations teams, network performance monitoring is central in ensuring application and infrastructure performance. If the network is sluggish, an application may also be slow, frustrating users. Worse, a malicious attacker may gain access to the network, compromising sensitive application data.














































Let's personalize your content