TTP-based threat hunting with Dynatrace Security Analytics and Falco Alerts solves alert noise
Dynatrace
AUGUST 9, 2023
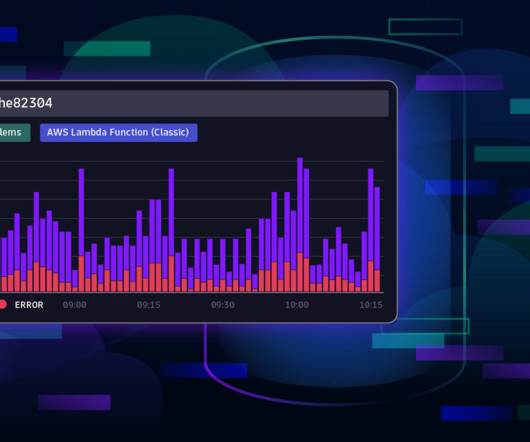
In this blog post, we’ll use Dynatrace Security Analytics to go threat hunting, bringing together logs, traces, metrics, and, crucially, threat alerts. Attack tactics describe why an attacker performs an action, for example, to get that first foothold into your network. It also generates OpenTelemetry traces.












































Let's personalize your content