Unlocking Efficiency: The Utility of Mini PCs in Virtualization
DZone
DECEMBER 20, 2023
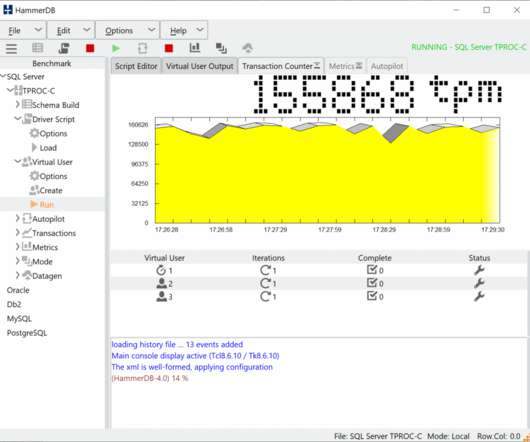
Virtualization has become a crucial element for companies and individuals looking to optimize their computing resources in today’s rapidly changing technological landscape. Mini PCs have become effective virtualization tools in this setting, providing a portable yet effective solution for a variety of applications.










































Let's personalize your content