Building Netflix’s Distributed Tracing Infrastructure
The Netflix TechBlog
OCTOBER 19, 2020
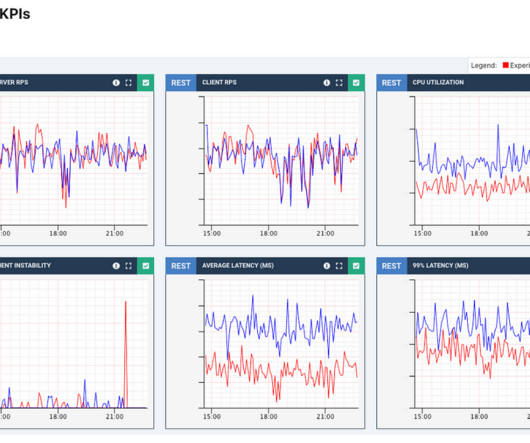
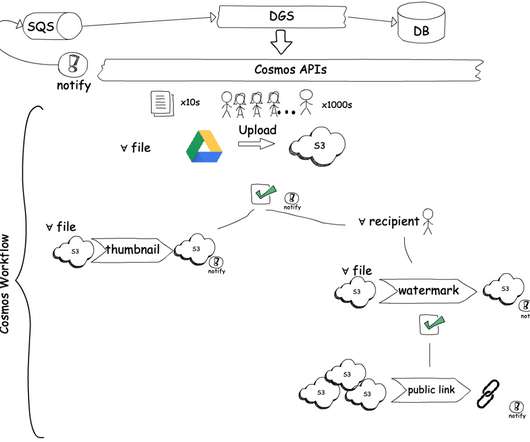
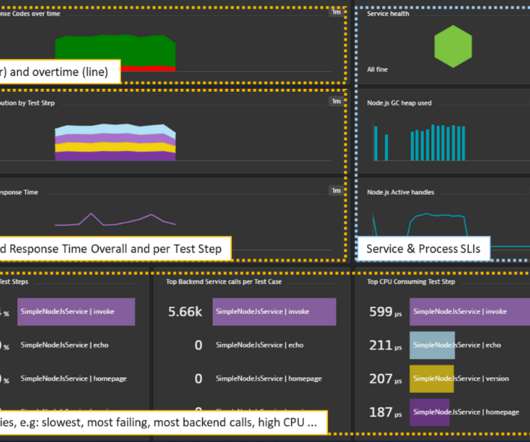
Now let’s look at how we designed the tracing infrastructure that powers Edgar. This insight led us to build Edgar: a distributed tracing infrastructure and user experience. Our tactical approach was to use Netflix-specific libraries for collecting traces from Java-based streaming services until open source tracer libraries matured.







































Let's personalize your content