Monitoring Web Servers Should Never Be Complex
DZone
SEPTEMBER 29, 2021
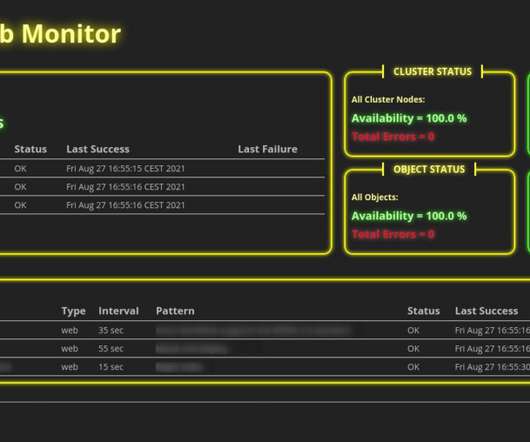
If you run several web servers in your organization or even public web servers on the internet, you need some kind of monitoring. For example, you can monitor the behavior of your applications, the hardware usage of your server nodes, or even the network traffic between servers. Introduction.
































Let's personalize your content