Designing Better Links For Websites And Emails: A Guideline
Smashing Magazine
DECEMBER 6, 2021
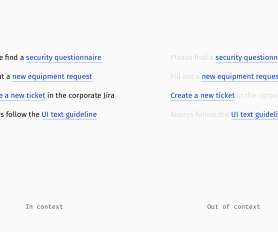
Designing Better Links For Websites And Emails: A Guideline. Designing Better Links For Websites And Emails: A Guideline. How many times have you encountered or composed the following on websites, in emails, or intranets? Download Links. Download Links. Download the recording”. Slava Shestopalov.









































Let's personalize your content