Running Ansible From Windows Using Virtualization
DZone
SEPTEMBER 6, 2023
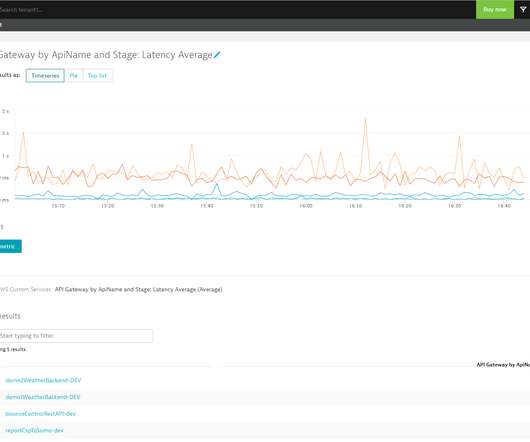
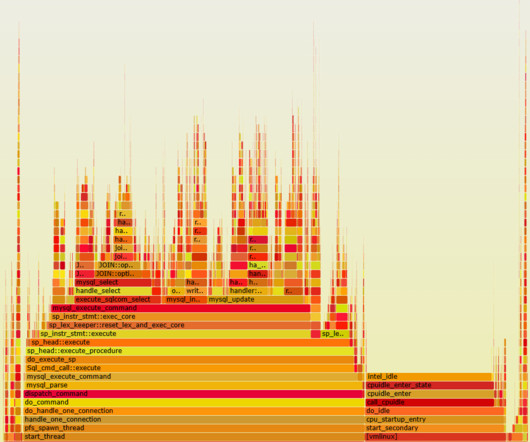
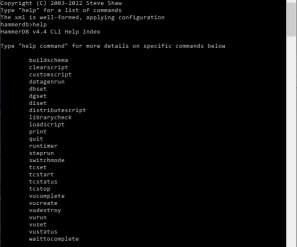
However, I found that WSL has this tendency to go haywire and use system resources such as CPU and RAM to the max. Since the virtual memory processes used to enable WSL are protected and cannot be killed or restarted, the only recourse is a good old Windows reboot. The steps I followed will be documented next.







































Let's personalize your content