Simplified image management: Dive into our end-to-end Harbor and Jenkins integration
Dynatrace
APRIL 24, 2024
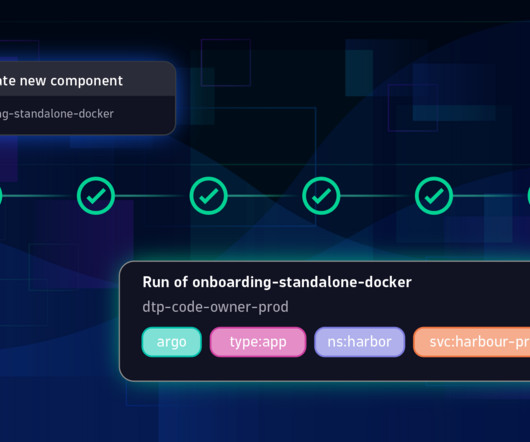
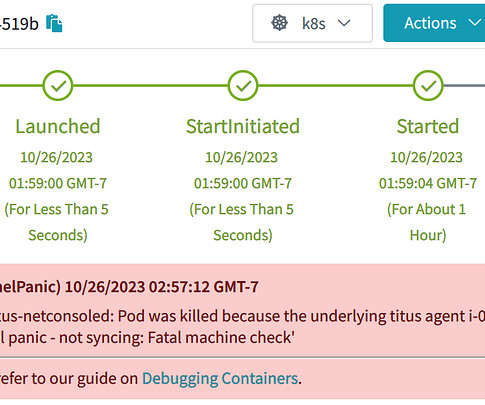
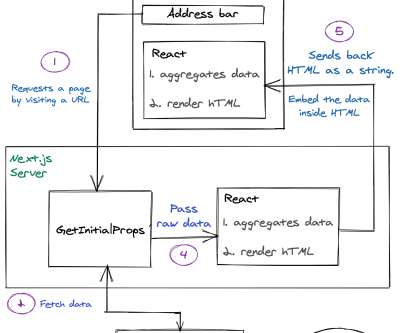
Simplified image management with our Harbor and Jenkins integration We’re excited to introduce our latest setup, aimed at streamlining the process of pushing images to Harbor. The setup can be further distributed to multiple other registries, like ECR or Azure/Google container registries.





































Let's personalize your content