What is security analytics?
Dynatrace
JUNE 10, 2024
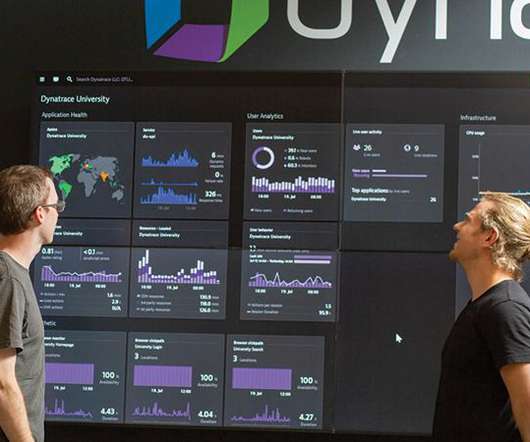
For example, an organization might use security analytics tools to monitor user behavior and network traffic. Security analytics solutions are designed to handle modern applications that rely on dynamic code and microservices. Infrastructure type In most cases, legacy SIEM tools are on-premises.









































Let's personalize your content