What is security analytics?
Dynatrace
JUNE 10, 2024
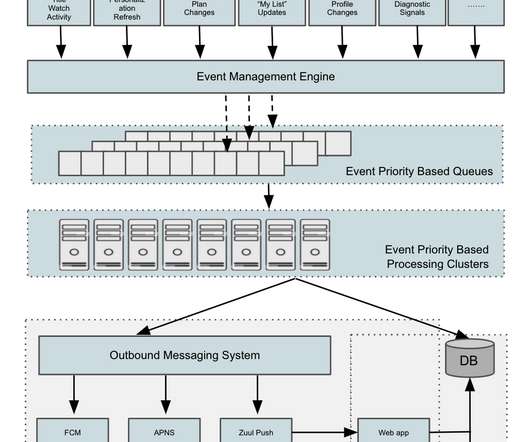
They can also develop proactive security measures capable of stopping threats before they breach network defenses. For example, an organization might use security analytics tools to monitor user behavior and network traffic. But, observability doesn’t stop at simply discovering data across your network.







































Let's personalize your content