Improved PHP monitoring with even less overhead!
Dynatrace
JULY 3, 2019
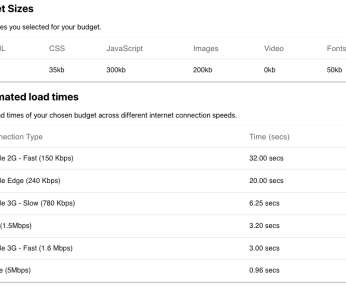
Here are some statistics: PHP now accounts for about 79% of the server-side programming used on the Internet. PHP-based WordPress boasts that it alone runs over one-third of the Internet (based on W3Techs statistics). Dynatrace improves AI-powered PHP monitoring. To benefit from enhanced PHP monitoring in Dynatrace.











































Let's personalize your content