Practical API Design at Netflix, Part 1: Using Protobuf FieldMask
The Netflix TechBlog
SEPTEMBER 3, 2021
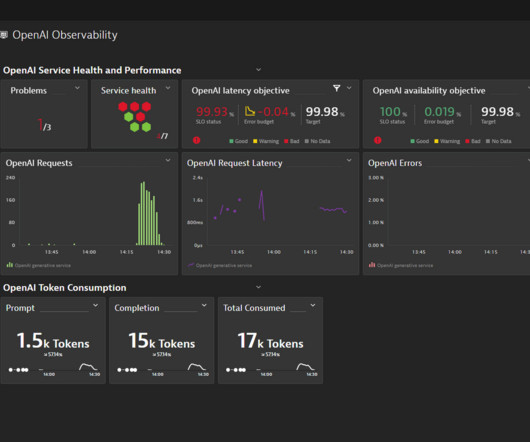
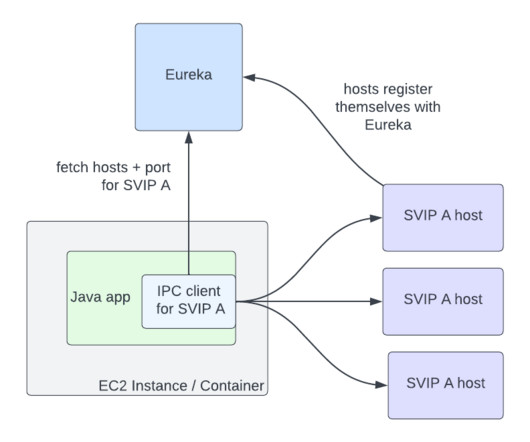
How can we achieve a similar functionality when designing our gRPC APIs? Add FieldMask to the Request Message Instead of creating one-off “include” fields, API designers can add field_mask field to the request message: [link] Consumers can set paths for the fields they expect to receive in the response. Field names are not included.





































Let's personalize your content