Best Practices To Secure Stateless REST Applications
DZone
FEBRUARY 26, 2024
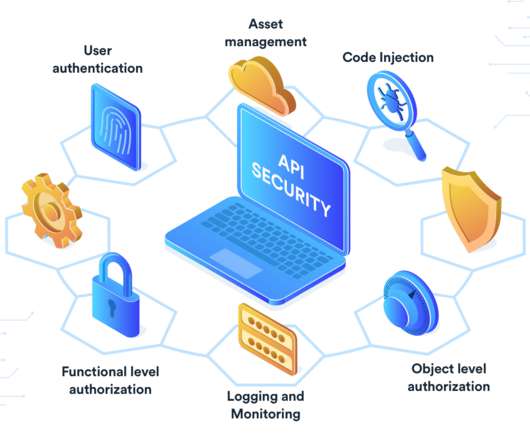
Statelessness in RESTful applications poses challenges and opportunities, influencing how we manage fundamental security aspects such as authentication and authorization. This blog aims to delve into this topic, explore its impact, and offer insights into the best practices for handling stateless REST applications.












































Let's personalize your content