Best practices for Fluent Bit 3.0
Dynatrace
MAY 7, 2024
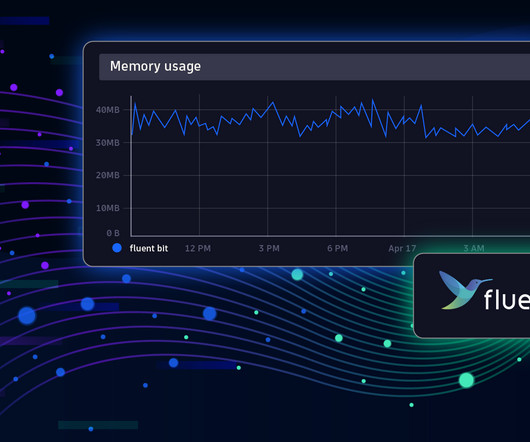
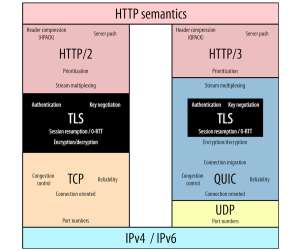
Fluent Bit was created before Kubernetes existed when Internet of Things (IoT) was a new buzzword. which offers a range of updates: HTTP/2 support: Fluentbit now supports HTTP/2, enabling efficient data transmission with Gzip compression for OpenTelemetry data, enhancing pipeline performance. Best practices for Fluent Bit 3.0


























Let's personalize your content